|
奥日的HP初始是三个小圆球。每个圆球浮点值10,三个是30。受到一次伤害减5,所以2个半圆球就是25。根据这个能尽快搜到地址。 ----------------- 灭小boss,奥日一刀下去,敌HP-8 一击必杀:找个血厚的小怪,设置浮点数,未知,减小,不变,减小等等,然后在最后实在无法再减少的结果中,找初始值为整数的。比如某个小怪HP为32。 然后找写入地址的代码,再找攻击值。在脚本中将攻击值改为浮点9999. ------------------------------ 黄球, 金钱或者经验值: 按照界面上值找到2个浮点值,修改后发现在游戏中无效。之后发现这两个值改大后会逐渐变回实际的黄球值。 于是找什么写入该地址,找到一个不停写入的代码,分析代码,在该代码上一层函数的代码中,找到 GameAssembly.dll+901AB9 - 8B 40 30 - mov eax,[rax+30] 经观察和修改,证实[rax+30]存放的是实际的黄球值,为4字节而不是浮点值!!! 所以,直接搜4字节的黄球值就可以。 ----------------------------------------- 查找3级跳: 假设是4字节,初始找未知初始值。 然后配备3级跳、卸载3级跳,在回到游戏界面以后,分别查找变动值。最终,找到一个地址类似:2338B08B644,4字节。 当配备3级跳时候该值为2,不配备则为1(为0则只能跳1下,后来学会连跳,此值为1;配备上3级跳,则此值为2)。 查找写入该地址指令,得到: 执行次数多(一)7FFAFA4D99E1 - FF 8B 94000000 - dec [rbx+00000094] 此指令明显是减1。 执行次数少(二)7FFAFA4DA980 - 89 83 94000000 - mov [rbx+00000094],eax 经过分析,(一)是按下跳跃按钮后执行的指令;(二)是程序判断奥日落地后执行的指令,此指令将奥日的跳跃次数赋值给地址。(一直没有追到eax中的跳跃次数值到底是哪里来的!!!) 经过试验得知,注销掉(一),就可以实现无限次数的跳跃飞翔!!!!!! 经过试验得知,注销掉(二),游戏判断触地后写入2次跳跃值失效!!!!!! 而相对更自由的方式是想要玩家自定义设置一个跳跃次数,实现玩家控制跳跃次数。 实现上述目标,可以注销掉(二),然后设置一个自定义值,这样每跳跃一次减1一次,一直到结果为0。可以实现精确控制跳跃次数。 ----------------------------------------- 查找单箭速射: 假定为4字节,不断装配和卸载速射,回到游戏界面不断查找变化值。 得到类似:1C504108F4C,装配为0,不装配为FFFFFFFF。 查找写入指令:1个是装配的,一个是卸载的。 下面是装配的指令:主要是将地址写入0,其中,edx==0 GameAssembly.dll+143A1A6: 7FFAE1F9A1A0 - 40 53 - push rbx 7FFAE1F9A1A2 - 48 83 EC 20 - sub rsp,20 7FFAE1F9A1A6 - 89 51 1C - mov [rcx+1C],edx << 7FFAE1F9A1A9 - 48 8B D9 - mov rbx,rcx 7FFAE1F9A1AC - 33 D2 - xor edx,edx ---------------------------------------------------- 猫头鹰三级跳飞查找: 按照精灵3级跳的套路,猜想该值为4字节,初始为2,起跳后仍为2,在空中第二次跳,则变1,第三次跳则变0,落地则变回2。 按此套路查找到类似 205BAB83864 地址。 查找写入该地址指令。 一条是在不跳的时候频繁写入2。 一条是dec指令。 ---------------------------------------------------- 挑战小游戏时间锁定查找: 用CE将游戏速度降到最低,以方便查看当前时间值。 然后搜索单浮点时间值。锁定即可。 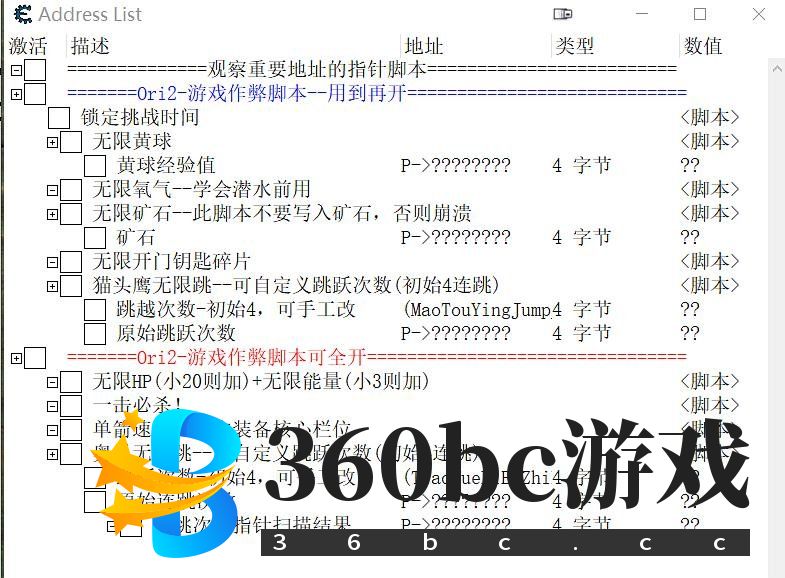 ct表中脚本实现无限HP,一击必杀,光箭速射不占栏位,无限跳跃、无限氧气、无限经验值、无限矿石、无限开门钥匙碎片,锁定挑战小游戏的时间等功能。 原则上所有脚本,也就是本ct表文件适用于游戏的任何版本,因为所有脚本都是aob注入(特征码)。 我的CE用CT修改表文件内容,包含在下面的: {{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{ }}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}} 之中,如果想使用的话,将上述括号中间的文字内容拷贝到记事本,并将记事本保存后,将扩展名txt改为ct,即可载入ce使用。 ct表文件内容:注意不要拷贝{{{{{{ 和 }}}}}这2行!!! {{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{ <?xml version="1.0" encoding="utf-8"?> <CheatTable CheatEngineTableVersion="42"> <CheatEntries> <CheatEntry> <ID>36</ID> <Description>"==============观察重要地址的指针脚本========================="</Description> <Options moAlwaysHideChildren="1" moManualExpandCollapse="1" moDeactivateChildrenAsWell="1"/> <GroupHeader>1</GroupHeader> <CheatEntries> <CheatEntry> <ID>41</ID> <Description>"查看HP"</Description> <Options moManualExpandCollapse="1"/> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>// Game Exe文件名 : oriandthewillofthewisps-pc.exe // Author : laoz // Exe 文件版本 : 2018.4.11.45208 // Module Version : // Script Date : 2022-05-14 // Created with : customAOBInjectionTemplates version: 1.3.9 [ENABLE] //注入点位置是频繁读取HP地址的指令。该指令是对xxxxxx进行查找什么改变这个地址操作得到的。 aobscanmodule(aob_ChaKanHP,GameAssembly.dll,8B 40 10 89 43 2C C6) registersymbol(aob_ChaKanHP) //这里ChaKanHP的意思是:查看HP alloc(newmem_ChaKanHP,256,GameAssembly.dll) label(return_ChaKanHP) //以下人造指针1 alloc(ChaKanHP_P,8) //人造指针8或4字节(64位需要8字节) registersymbol(ChaKanHP_P) // //以上人造指针1 //以下人造指针2 alloc(ChaKanHP_P_xx2,8) //人造指针,xx2可自己修改为HP或子弹等 registersymbol(ChaKanHP_P_xx2) // //以上人造指针2 newmem_ChaKanHP: //以下进行人造指针------------------------------------------------ mov [ChaKanHP_P],rax //以上进行人造指针------------------------------------------------ //下面放置新增代码 //------------------------------------------------------------------- //------------------------------------------------------------------- //以下为原代码 mov eax,[rax+10] mov [rbx+2C],eax jmp return_ChaKanHP aob_ChaKanHP: jmp newmem_ChaKanHP nop return_ChaKanHP: [DISABLE] aob_ChaKanHP: db 8B 40 10 89 43 2C unregistersymbol(*) dealloc(*) { // ORIGINAL CODE - INJECTION POINT: GameAssembly.dll+F141D5 GameAssembly.dll+F141C0: 33 D2 - xor edx,edx GameAssembly.dll+F141C2: E8 79 AD 51 00 - call GameAssembly.dll+142EF40 GameAssembly.dll+F141C7: 48 85 C0 - test rax,rax GameAssembly.dll+F141CA: 74 30 - je GameAssembly.dll+F141FC GameAssembly.dll+F141CC: 48 8B 40 28 - mov rax,[rax+28] GameAssembly.dll+F141D0: 48 85 C0 - test rax,rax GameAssembly.dll+F141D3: 74 21 - je GameAssembly.dll+F141F6 // ---------- INJECTING HERE ---------- GameAssembly.dll+F141D5: 8B 40 10 - mov eax,[rax+10] // ---------- DONE INJECTING ---------- GameAssembly.dll+F141D8: 89 43 2C - mov [rbx+2C],eax GameAssembly.dll+F141DB: C6 43 28 00 - mov byte ptr [rbx+28],00 GameAssembly.dll+F141DF: F3 0F 10 43 2C - movss xmm0,[rbx+2C] GameAssembly.dll+F141E4: 48 83 C4 40 - add rsp,40 GameAssembly.dll+F141E8: 5B - pop rbx GameAssembly.dll+F141E9: C3 - ret } </AssemblerScript> <CheatEntries> <CheatEntry> <ID>42</ID> <Description>"HP当前最大值??"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>ChaKanHP_P</Address> <Offsets> <Offset>14</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>40</ID> <Description>"HP"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>ChaKanHP_P</Address> <Offsets> <Offset>10</Offset> </Offsets> </CheatEntry> </CheatEntries> </CheatEntry> <CheatEntry> <ID>66</ID> <Description>"查看能量值"</Description> <Options moManualExpandCollapse="1"/> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>// Game Exe文件名 : oriandthewillofthewisps-pc.exe // Author : laoz // Exe 文件版本 : 2018.4.11.45208 // Module Version : // Script Date : 2022-05-14 // Created with : customAOBInjectionTemplates version: 1.3.9 [ENABLE] //注入点位置是某频繁访问能量值指令。 aobscanmodule(aob_GuanChaNengLiangZhi,GameAssembly.dll,F3 0F 11 43 28 0F 28 74 24 60) registersymbol(aob_GuanChaNengLiangZhi) //意思是:观察能量值 alloc(newmem_GuanChaNengLiangZhi,256,GameAssembly.dll) label(return_GuanChaNengLiangZhi) //以下人造指针1 alloc(GuanChaNengLiangZhi_P,8) //人造指针8或4字节(64位需要8字节) registersymbol(GuanChaNengLiangZhi_P) // //以上人造指针1 //以下人造指针2 alloc(GuanChaNengLiangZhi_P_xx2,8) //人造指针,xx2可自己修改为HP或子弹等 registersymbol(GuanChaNengLiangZhi_P_xx2) // //以上人造指针2 newmem_GuanChaNengLiangZhi: //以下进行人造指针------------------------------------------------ mov [GuanChaNengLiangZhi_P],rbx //以上进行人造指针------------------------------------------------ //下面放置新增代码 //------------------------------------------------------------------- //------------------------------------------------------------------- //以下为原代码 movss [rbx+28],xmm0 jmp return_GuanChaNengLiangZhi aob_GuanChaNengLiangZhi: jmp newmem_GuanChaNengLiangZhi return_GuanChaNengLiangZhi: [DISABLE] aob_GuanChaNengLiangZhi: db F3 0F 11 43 28 unregistersymbol(*) dealloc(*) { // ORIGINAL CODE - INJECTION POINT: GameAssembly.dll+9706E9 GameAssembly.dll+9706CA: 48 85 C0 - test rax,rax GameAssembly.dll+9706CD: 74 35 - je GameAssembly.dll+970704 GameAssembly.dll+9706CF: 48 89 05 4A DF A8 03 - mov [GameAssembly.dll+43FE620],rax GameAssembly.dll+9706D6: FF D0 - call rax GameAssembly.dll+9706D8: 45 33 C9 - xor r9d,r9d GameAssembly.dll+9706DB: 0F 28 D0 - movaps xmm2,xmm0 GameAssembly.dll+9706DE: 0F 28 CF - movaps xmm1,xmm7 GameAssembly.dll+9706E1: 0F 28 C6 - movaps xmm0,xmm6 GameAssembly.dll+9706E4: E8 27 4C 74 01 - call GameAssembly.dll+20B5310 // ---------- INJECTING HERE ---------- GameAssembly.dll+9706E9: F3 0F 11 43 28 - movss [rbx+28],xmm0 // ---------- DONE INJECTING ---------- GameAssembly.dll+9706EE: 0F 28 74 24 60 - movaps xmm6,[rsp+60] GameAssembly.dll+9706F3: 0F 28 7C 24 50 - movaps xmm7,[rsp+50] GameAssembly.dll+9706F8: 44 0F 28 44 24 40 - movaps xmm8,[rsp+40] GameAssembly.dll+9706FE: 48 83 C4 70 - add rsp,70 GameAssembly.dll+970702: 5B - pop rbx GameAssembly.dll+970703: C3 - ret } </AssemblerScript> <CheatEntries> <CheatEntry> <ID>67</ID> <Description>"能量值-非实际能量值,为参考地址"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>GuanChaNengLiangZhi_P</Address> <Offsets> <Offset>28</Offset> </Offsets> </CheatEntry> </CheatEntries> </CheatEntry> <CheatEntry> <ID>105</ID> <Description>"===============老版本--简练-功能少============================="</Description> <Options moManualExpandCollapse="1"/> <GroupHeader>1</GroupHeader> <CheatEntries> <CheatEntry> <ID>91</ID> <Description>"一击必杀待更新-加显示敌HP-老的脚本"</Description> <Options moManualExpandCollapse="1"/> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>// Game Exe文件名 : oriandthewillofthewisps-pc.exe // Author : laoz // Exe 文件版本 : 2018.4.11.45208 // Module Version : // Script Date : 2022-05-14 // Created with : customAOBInjectionTemplates version: 1.3.9 [ENABLE] //注入点位置是对敌人减HP指令。该指令是对敌人HP地址进行查找什么改变这个地址操作得到的。 aobscanmodule(aob_YiJiBiShaA,GameAssembly.dll,F3 0F 5C CA 4C 8B 80 80 02 00 00) registersymbol(aob_YiJiBiShaA) //YiJiBiShaA是:一击必杀 alloc(newmem_YiJiBiShaA,256,GameAssembly.dll) label(return_YiJiBiShaA) //以下 alloc(YiJiBiShaA_temp,4) //人造指针8或4字节(64位需要8字节) registersymbol(YiJiBiShaA_temp) // //以上 //以下人造指针2 alloc(YiJiBiShaA_P_xx2,4) //人造指针,xx2可自己修改为HP或子弹等 registersymbol(YiJiBiShaA_P_xx2) // //以上人造指针2 //以下人造指针3 alloc(YiJiBiShaA_P_xx3,8) //人造指针,敌人的HP registersymbol(YiJiBiShaA_P_xx3) // //以上人造指针3 label(YiJiBiShaA_YuanDaiMa) newmem_YiJiBiShaA: //以下进行人造指针------------------------------------------------ movss [YiJiBiShaA_P_xx2],xmm2 //实际的攻击值 mov [YiJiBiShaA_P_xx3],rdi //rdi+28为敌HP地址 //以上进行人造指针------------------------------------------------ //下面放置新增代码 //------------------------------------------------------------------- cmp [YiJiBiShaA_temp],0 jnz YiJiBiShaA_YuanDaiMa push r14 //不能从寄存器到浮点寄存器,因此须用内存中转 mov r14,(float)99999 //攻击值放到r14 mov [YiJiBiShaA_temp],r14 //从r14中转到临时地址,这个可做为可观察的当前巨大攻击值 pop r14 YiJiBiShaA_YuanDaiMa: movss xmm2,[YiJiBiShaA_temp]//从临时地址到xmm2 //------------------------------------------------------------------- //以下为原代码 subss xmm1,xmm2 mov r8,[rax+00000280] jmp return_YiJiBiShaA aob_YiJiBiShaA: jmp newmem_YiJiBiShaA nop 6 return_YiJiBiShaA: [DISABLE] aob_YiJiBiShaA: db F3 0F 5C CA 4C 8B 80 80 02 00 00 unregistersymbol(*) dealloc(*) { // ORIGINAL CODE - INJECTION POINT: GameAssembly.dll+B63FEA GameAssembly.dll+B63FD0: 0F 11 45 E7 - movups [rbp-19],xmm0 GameAssembly.dll+B63FD4: F2 0F 10 4B 20 - movsd xmm1,[rbx+20] GameAssembly.dll+B63FD9: F2 0F 11 4D F7 - movsd [rbp-09],xmm1 GameAssembly.dll+B63FDE: 48 8B 07 - mov rax,[rdi] GameAssembly.dll+B63FE1: F3 0F 10 4F 28 - movss xmm1,[rdi+28] GameAssembly.dll+B63FE6: 0F C6 D2 AA - shufps xmm2,xmm2,-56 // ---------- INJECTING HERE ---------- GameAssembly.dll+B63FEA: F3 0F 5C CA - subss xmm1,xmm2 // ---------- DONE INJECTING ---------- GameAssembly.dll+B63FEE: 4C 8B 80 80 02 00 00 - mov r8,[rax+00000280] GameAssembly.dll+B63FF5: 48 8B CF - mov rcx,rdi GameAssembly.dll+B63FF8: FF 90 78 02 00 00 - call qword ptr [rax+00000278] GameAssembly.dll+B63FFE: 4C 8B 77 48 - mov r14,[rdi+48] GameAssembly.dll+B64002: 48 8B 0D B7 6C 83 03 - mov rcx,[GameAssembly.dll+439ACC0] GameAssembly.dll+B64009: F6 81 27 01 00 00 02 - test byte ptr [rcx+00000127],02 GameAssembly.dll+B64010: 74 0E - je GameAssembly.dll+B64020 GameAssembly.dll+B64012: 83 B9 D8 00 00 00 00 - cmp dword ptr [rcx+000000D8],00 GameAssembly.dll+B64019: 75 05 - jne GameAssembly.dll+B64020 GameAssembly.dll+B6401B: E8 E0 9A 6E FF - call GameAssembly.dll+24DB00 } </AssemblerScript> <CheatEntries> <CheatEntry> <ID>92</ID> <Description>"敌HP"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>YiJiBiShaA_P_xx3</Address> <Offsets> <Offset>28</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>93</ID> <Description>"脚本给的巨大攻击值"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>YiJiBiShaA_temp</Address> </CheatEntry> <CheatEntry> <ID>94</ID> <Description>"实际攻击值"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>YiJiBiShaA_P_xx2</Address> </CheatEntry> </CheatEntries> </CheatEntry> <CheatEntry> <ID>64</ID> <Description>"无限能量"</Description> <Options moManualExpandCollapse="1"/> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>// Game Exe文件名 : oriandthewillofthewisps-pc.exe // Author : laoz // Exe 文件版本 : 2018.4.11.45208 // Module Version : // Script Date : 2022-05-14 // Created with : customAOBInjectionTemplates version: 1.3.9 [ENABLE] //注入点位置是减少能量指令。该指令是对能量地址进行查找什么改变这个地址操作得到的。 aobscanmodule(aob_NengLiang,GameAssembly.dll,F3 0F 11 73 18 33) registersymbol(aob_NengLiang) //这里NengLiang的意思是:能量 alloc(newmem_NengLiang,256,GameAssembly.dll) label(return_NengLiang) //以下人造指针1 alloc(NengLiang_P,8) //人造指针8或4字节(64位需要8字节) registersymbol(NengLiang_P) // //以上人造指针1 //以下人造指针2 alloc(NengLiang_P_xx2,8) //人造指针,xx2可自己修改为HP或子弹等 registersymbol(NengLiang_P_xx2) // //以上人造指针2 newmem_NengLiang: //以下进行人造指针------------------------------------------------ mov [NengLiang_P],rbx //以上进行人造指针------------------------------------------------ //下面放置新增代码 //------------------------------------------------------------------- movss [rbx+18],xmm0 //经观察,发现xmm0是当前能量上限最大值 //------------------------------------------------------------------- //以下为原代码 //movss [rbx+18],xmm6 jmp return_NengLiang aob_NengLiang: jmp newmem_NengLiang return_NengLiang: [DISABLE] aob_NengLiang: db F3 0F 11 73 18 unregistersymbol(*) dealloc(*) { // ORIGINAL CODE - INJECTION POINT: GameAssembly.dll+96EA4D GameAssembly.dll+96EA3E: 76 08 - jna GameAssembly.dll+96EA48 GameAssembly.dll+96EA40: 0F 28 F7 - movaps xmm6,xmm7 GameAssembly.dll+96EA43: EB 03 - jmp GameAssembly.dll+96EA48 GameAssembly.dll+96EA45: 0F 57 F6 - xorps xmm6,xmm6 GameAssembly.dll+96EA48: 48 85 DB - test rbx,rbx GameAssembly.dll+96EA4B: 74 34 - je GameAssembly.dll+96EA81 // ---------- INJECTING HERE ---------- GameAssembly.dll+96EA4D: F3 0F 11 73 18 - movss [rbx+18],xmm6 // ---------- DONE INJECTING ---------- GameAssembly.dll+96EA52: 33 D2 - xor edx,edx GameAssembly.dll+96EA54: 48 8B CB - mov rcx,rbx GameAssembly.dll+96EA57: E8 74 C7 AC 00 - call GameAssembly.dll+143B1D0 GameAssembly.dll+96EA5C: C6 47 30 01 - mov byte ptr [rdi+30],01 GameAssembly.dll+96EA60: 48 8B 5C 24 70 - mov rbx,[rsp+70] } </AssemblerScript> </CheatEntry> <CheatEntry> <ID>137</ID> <Description>"无限能量-且HP小于2个球自动充满"</Description> <Options moManualExpandCollapse="1"/> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>// Game Exe文件名 : oriandthewillofthewisps-pc.exe // Author : laoz // Exe 文件版本 : 2018.4.11.45208 // Module Version : // Script Date : 2022-05-14 // Created with : customAOBInjectionTemplates version: 1.3.9 [ENABLE] //注入点位置是减少能量指令。该指令是对能量地址进行查找什么改变这个地址操作得到的。 aobscanmodule(aob_NengLiang,GameAssembly.dll,F3 0F 11 73 18 33) registersymbol(aob_NengLiang) //这里NengLiang的意思是:能量 alloc(newmem_NengLiang,256,GameAssembly.dll) label(return_NengLiang) //以下人造指针1 alloc(NengLiang_P,8) //人造指针8或4字节(64位需要8字节) registersymbol(NengLiang_P) // //以上人造指针1 //以下人造指针2 alloc(NengLiang_P_temp,8) //人造指针,xx2可自己修改为HP或子弹等 registersymbol(NengLiang_P_temp) // //以上人造指针2 label(return_NengLiang_YDM) //原代码 newmem_NengLiang: //以下进行人造指针------------------------------------------------ mov [NengLiang_P],rbx //以上进行人造指针------------------------------------------------ cmp [rbx+10],(float)20 //奥日HP的值和20比较 //HP大于或等于20跳转到:return_NengLiang_YDM :原代码 jae return_NengLiang_YDM //原代码 //小于20则执行以下指令,给HP加到当前最大值 //mov [rbx+10],(float)100 //下面的语句其实简单就这一句 push rax //保护eax,因要用eax中转(因为mov不能内存到内存)。 mov eax,[rbx+14] //rbx+14存放HP最大值,但是是4字节值,须转为浮点数 cvtsi2ss XMM15,eax //将m32转为32位单浮点数! 放到xmm15的第一位置 movss [NengLiang_P_temp],xmm15 //将浮点数存入内存地址中转 mov eax,[NengLiang_P_temp] //将中转内存地址值用eax中转 mov [rbx+10],eax pop rax //xor xmm15,xmm15 return_NengLiang_YDM: //原代码 //下面放置新增代码 //------------------------------------------------------------------- movss [rbx+18],xmm0 //经观察,发现xmm0是当前能量上限最大值 //------------------------------------------------------------------- //以下为原代码 //movss [rbx+18],xmm6 jmp return_NengLiang aob_NengLiang: jmp newmem_NengLiang return_NengLiang: [DISABLE] aob_NengLiang: db F3 0F 11 73 18 unregistersymbol(*) dealloc(*) { // ORIGINAL CODE - INJECTION POINT: GameAssembly.dll+96EA4D GameAssembly.dll+96EA3E: 76 08 - jna GameAssembly.dll+96EA48 GameAssembly.dll+96EA40: 0F 28 F7 - movaps xmm6,xmm7 GameAssembly.dll+96EA43: EB 03 - jmp GameAssembly.dll+96EA48 GameAssembly.dll+96EA45: 0F 57 F6 - xorps xmm6,xmm6 GameAssembly.dll+96EA48: 48 85 DB - test rbx,rbx GameAssembly.dll+96EA4B: 74 34 - je GameAssembly.dll+96EA81 // ---------- INJECTING HERE ---------- GameAssembly.dll+96EA4D: F3 0F 11 73 18 - movss [rbx+18],xmm6 // ---------- DONE INJECTING ---------- GameAssembly.dll+96EA52: 33 D2 - xor edx,edx GameAssembly.dll+96EA54: 48 8B CB - mov rcx,rbx GameAssembly.dll+96EA57: E8 74 C7 AC 00 - call GameAssembly.dll+143B1D0 GameAssembly.dll+96EA5C: C6 47 30 01 - mov byte ptr [rdi+30],01 GameAssembly.dll+96EA60: 48 8B 5C 24 70 - mov rbx,[rsp+70] } </AssemblerScript> <CheatEntries> <CheatEntry> <ID>65</ID> <Description>"能量当前上限"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>NengLiang_P</Address> <Offsets> <Offset>1C</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>68</ID> <Description>"能量-1个球是浮点1"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>NengLiang_P</Address> <Offsets> <Offset>18</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>109</ID> <Description>"HP当前上限"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>NengLiang_P</Address> <Offsets> <Offset>14</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>108</ID> <Description>"HP"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>NengLiang_P</Address> <Offsets> <Offset>10</Offset> </Offsets> <CheatEntries> <CheatEntry> <ID>138</ID> <Description>"HP指针扫描结果"</Description> <Options moAlwaysHideChildren="1" moManualExpandCollapse="1"/> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+04383FC0</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>18</Offset> <Offset>20</Offset> <Offset>B8</Offset> </Offsets> <CheatEntries> <CheatEntry> <ID>139</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+043BB910</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>18</Offset> <Offset>10</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>140</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+0438D168</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>18</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>141</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+04392510</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>38</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>142</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+043D6F00</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>38</Offset> <Offset>30</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>143</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+0438F680</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>38</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>144</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+0435B2D8</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>48</Offset> <Offset>20</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>145</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+043B7A68</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>48</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>146</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+043870F0</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>88</Offset> <Offset>30</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>147</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+04353068</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>88</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>148</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+0438D5E8</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>D8</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>149</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+04383BA0</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>D8</Offset> <Offset>100</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>150</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+04354850</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>D8</Offset> <Offset>C0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>151</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+043BD470</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>D8</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>152</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+0439A960</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>128</Offset> <Offset>8</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>153</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+0438E6C0</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>128</Offset> <Offset>C8</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>154</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+043ABD70</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>128</Offset> <Offset>128</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>155</ID> <Description>"指针扫描结果"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+043D70A0</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>178</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> </CheatEntries> </CheatEntry> </CheatEntries> </CheatEntry> </CheatEntries> </CheatEntry> <CheatEntry> <ID>52</ID> <Description>"无限HP"</Description> <Options moAlwaysHideChildren="1" moManualExpandCollapse="1"/> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>// Game Exe文件名 : oriandthewillofthewisps-pc.exe // Author : laoz // Exe 文件版本 : 2018.4.11.45208 // Module Version : // Script Date : 2022-05-13 // Created with : customAOBInjectionTemplates version: 1.3.9 [ENABLE] //注入点位置是写精灵HP的指令。该指令是对HP进行查找什么改变这个地址操作得到的。 aobscanmodule(aob_ori2_HP,GameAssembly.dll,89 41 10 33 D2 0F) registersymbol(aob_ori2_HP) //这里ori2_HP的意思是:奥日2——HP alloc(newmem_ori2_HP,256,GameAssembly.dll) label(return_ori2_HP) //以下人造指针1 alloc(ori2_HP_P,8) //人造指针8或4字节(64位需要8字节) registersymbol(ori2_HP_P) //奥日2——HP的人造指针 //以上人造指针1 //以下临时变量 alloc(ori2_HP_P_xx2,8) //临时变量,存放中转的HP最大值 registersymbol(ori2_HP_P_xx2) // //以上临时变量 newmem_ori2_HP: //以下进行人造指针------------------------------------------------ mov [ori2_HP_P],rcx //以上进行人造指针------------------------------------------------ //下面放置新增代码 //------------------------------------------------------------------- //mov eax,(float)90 mov eax,[rcx+14] //rcx+14位置是当前最大HP值(十六进制的),需转为浮点数 cvtsi2ss XMM15,eax //将m32转为32位单浮点数! 放到xmm15的第一位置 //cvtsi2sd XMM15,eax //2ss转为64位?xmm15第一位置清零,第一+第二=128位双浮点数? //movsd [ori2_HP_P_xx2],xmm15 movss [ori2_HP_P_xx2],xmm15 mov eax,[ori2_HP_P_xx2] //------------------------------------------------------------------- //以下为原代码 mov [rcx+10],eax xor edx,edx jmp return_ori2_HP aob_ori2_HP: jmp newmem_ori2_HP return_ori2_HP: [DISABLE] aob_ori2_HP: db 89 41 10 33 D2 unregistersymbol(*) dealloc(*) { // ORIGINAL CODE - INJECTION POINT: GameAssembly.dll+F14304 GameAssembly.dll+F142F6: 74 37 - je GameAssembly.dll+F1432F GameAssembly.dll+F142F8: 48 8B 48 28 - mov rcx,[rax+28] GameAssembly.dll+F142FC: 48 85 C9 - test rcx,rcx GameAssembly.dll+F142FF: 74 28 - je GameAssembly.dll+F14329 GameAssembly.dll+F14301: 8B 43 2C - mov eax,[rbx+2C] // ---------- INJECTING HERE ---------- GameAssembly.dll+F14304: 89 41 10 - mov [rcx+10],eax // ---------- DONE INJECTING ---------- GameAssembly.dll+F14307: 33 D2 - xor edx,edx GameAssembly.dll+F14309: 0F 28 74 24 50 - movaps xmm6,[rsp+50] GameAssembly.dll+F1430E: 0F 28 7C 24 40 - movaps xmm7,[rsp+40] GameAssembly.dll+F14313: 48 83 C4 60 - add rsp,60 GameAssembly.dll+F14317: 5B - pop rbx } </AssemblerScript> <CheatEntries> <CheatEntry> <ID>107</ID> <Description>"能量值当前上限"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>ori2_HP_P</Address> <Offsets> <Offset>1C</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>106</ID> <Description>"能量值"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>ori2_HP_P</Address> <Offsets> <Offset>18</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>53</ID> <Description>"HP当前上限"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>ori2_HP_P</Address> <Offsets> <Offset>14</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>22</ID> <Description>"HP-1个球浮点10,初始30"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>ori2_HP_P</Address> <Offsets> <Offset>10</Offset> </Offsets> </CheatEntry> </CheatEntries> </CheatEntry> <CheatEntry> <ID>216</ID> <Description>"跳跃第一条指令注销实现连跳"</Description> <Options moAlwaysHideChildren="1" moManualExpandCollapse="1"/> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>// Game Exe文件名 : oriandthewillofthewisps-pc.exe // Author : laoz // Exe 文件版本 : 2018.4.11.45208 // Module Version : // Script Date : 2022-05-20 // Created with : customAOBInjectionTemplates version: 1.3.9 [ENABLE] //注入点位置是减少跳跃次数指令。该指令是对xxxxxx进行查找什么改变这个地址操作得到的。 aobscanmodule(aob_WuXianLianTiao,GameAssembly.dll,FF 8B 94 00 00 00) registersymbol(aob_WuXianLianTiao) //这里WuXianLianTiao的意思是:无限连跳 alloc(newmem_WuXianLianTiao,256,GameAssembly.dll) label(return_WuXianLianTiao) //以下人造指针1 alloc(WuXianLianTiao_P,8) //人造指针8或4字节(64位需要8字节) registersymbol(WuXianLianTiao_P) // //以上人造指针1 //以下人造指针2 alloc(WuXianLianTiao_P_xx2,8) //人造指针,xx2可自己修改为HP或子弹等 registersymbol(WuXianLianTiao_P_xx2) // //以上人造指针2 newmem_WuXianLianTiao: //以下进行人造指针------------------------------------------------ mov [WuXianLianTiao_P],rbx //以上进行人造指针------------------------------------------------ //下面放置新增代码 //------------------------------------------------------------------- //------------------------------------------------------------------- //以下为原代码 //dec [rbx+00000094] //注销掉减一指令 jmp return_WuXianLianTiao aob_WuXianLianTiao: jmp newmem_WuXianLianTiao nop return_WuXianLianTiao: [DISABLE] aob_WuXianLianTiao: db FF 8B 94 00 00 00 unregistersymbol(*) dealloc(*) { // ORIGINAL CODE - INJECTION POINT: GameAssembly.dll+9699E1 GameAssembly.dll+9699BE: 0F 84 8F 09 00 00 - je GameAssembly.dll+96A353 GameAssembly.dll+9699C4: 48 8B 48 18 - mov rcx,[rax+18] GameAssembly.dll+9699C8: 48 85 C9 - test rcx,rcx GameAssembly.dll+9699CB: 0F 84 7C 09 00 00 - je GameAssembly.dll+96A34D GameAssembly.dll+9699D1: 45 33 C0 - xor r8d,r8d GameAssembly.dll+9699D4: F3 0F 10 8B 80 00 00 00 - movss xmm1,[rbx+00000080] GameAssembly.dll+9699DC: E8 1F C8 7B 00 - call GameAssembly.dll+1126200 // ---------- INJECTING HERE ---------- GameAssembly.dll+9699E1: FF 8B 94 00 00 00 - dec [rbx+00000094] // ---------- DONE INJECTING ---------- GameAssembly.dll+9699E7: 48 8B 43 58 - mov rax,[rbx+58] GameAssembly.dll+9699EB: 48 85 C0 - test rax,rax GameAssembly.dll+9699EE: 0F 84 53 09 00 00 - je GameAssembly.dll+96A347 GameAssembly.dll+9699F4: 48 8B 40 30 - mov rax,[rax+30] GameAssembly.dll+9699F8: 48 85 C0 - test rax,rax GameAssembly.dll+9699FB: 0F 84 40 09 00 00 - je GameAssembly.dll+96A341 GameAssembly.dll+969A01: 48 8B 48 50 - mov rcx,[rax+50] GameAssembly.dll+969A05: 48 85 C9 - test rcx,rcx } </AssemblerScript> <CheatEntries> <CheatEntry> <ID>217</ID> <Description>"原始连跳次数"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>WuXianLianTiao_P</Address> <Offsets> <Offset>94</Offset> </Offsets> </CheatEntry> </CheatEntries> </CheatEntry> <CheatEntry> <ID>224</ID> <Description>"跳跃第二指令注销后跳跃次数不再被写入2"</Description> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>[ENABLE] //注入点位置是写入跳跃次数的第二条指令。该指令判断落地后,写入奥日的可跳跃次数。 aobscanmodule(aob_TiaoYueDiErZhiLing,GameAssembly.dll,FF FF 89 83 94 00 00 00) registersymbol(aob_TiaoYueDiErZhiLing) //意思是:跳跃第二条指令 alloc(newmem_TiaoYueDiErZhiLing,256,GameAssembly.dll) label(return_TiaoYueDiErZhiLing) newmem_TiaoYueDiErZhiLing: //------------------------------------------------------------------- //以下为原代码 //mov [rbx+00000094],eax //注销掉本句指令,则原始的2跳跃值不再写入。 jmp return_TiaoYueDiErZhiLing aob_TiaoYueDiErZhiLing+02: jmp newmem_TiaoYueDiErZhiLing nop return_TiaoYueDiErZhiLing: [DISABLE] aob_TiaoYueDiErZhiLing+02: db 89 83 94 00 00 00 unregistersymbol(*) dealloc(*) { // ORIGINAL CODE - INJECTION POINT: GameAssembly.dll+96A980 GameAssembly.dll+96A97B: E8 90 E5 FF FF - call GameAssembly.dll+968F10 // ---------- INJECTING HERE ---------- GameAssembly.dll+96A980: 89 83 94 00 00 00 - mov [rbx+00000094],eax // ---------- DONE INJECTING ---------- GameAssembly.dll+96A986: 48 83 C4 40 - add rsp,40 GameAssembly.dll+96A98A: 5B - pop rbx GameAssembly.dll+96A98B: C3 - ret } </AssemblerScript> </CheatEntry> </CheatEntries> </CheatEntry> </CheatEntries> </CheatEntry> <CheatEntry> <ID>38</ID> <Description>"=======Ori2-游戏作弊脚本--用到再开============================"</Description> <Options moManualExpandCollapse="1"/> <Color>FF0000</Color> <GroupHeader>1</GroupHeader> <CheatEntries> <CheatEntry> <ID>297</ID> <Description>"锁定挑战时间"</Description> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>// Game Exe文件名 : oriandthewillofthewisps-pc.exe // Author : laoz // Exe 文件版本 : 2018.4.11.45208 // Module Version : // Script Date : 2022-05-22 // Created with : customAOBInjectionTemplates version: 1.3.9 [ENABLE] //注入点位置是锁定挑战时间的指令。该指令是对试炼时候时间进行查找什么改变这个地址操作得到的。 aobscanmodule(aob_LengQueTiaoZhanTime,GameAssembly.dll,F3 0F 11 43 18 0F 2F C1) registersymbol(aob_LengQueTiaoZhanTime) //这里LengQueTiaoZhanTime是:冷却挑战时间 alloc(newmem_LengQueTiaoZhanTime,256,GameAssembly.dll) label(return_LengQueTiaoZhanTime) //以下人造指针1 alloc(LengQueTiaoZhanTime_P_xx1,8) //人造指针8或4字节(64位需要8字节) registersymbol(LengQueTiaoZhanTime_P_xx1) // //以上人造指针1 //以下人造指针2 alloc(LengQueTiaoZhanTime_P_xx2,8) //人造指针,xx2可自己修改为HP或子弹等 registersymbol(LengQueTiaoZhanTime_P_xx2) // //以上人造指针2 newmem_LengQueTiaoZhanTime: //以下进行人造指针------------------------------------------------ //以上进行人造指针------------------------------------------------ //下面放置新增代码 //------------------------------------------------------------------- //------------------------------------------------------------------- //以下为原代码 //movss [rbx+18],xmm0 jmp return_LengQueTiaoZhanTime aob_LengQueTiaoZhanTime: jmp newmem_LengQueTiaoZhanTime return_LengQueTiaoZhanTime: [DISABLE] aob_LengQueTiaoZhanTime: db F3 0F 11 43 18 unregistersymbol(*) dealloc(*) { // ORIGINAL CODE - INJECTION POINT: GameAssembly.dll+9BDF0F GameAssembly.dll+9BDEFB: F3 0F 10 53 20 - movss xmm2,[rbx+20] GameAssembly.dll+9BDF00: F3 0F 58 C6 - addss xmm0,xmm6 GameAssembly.dll+9BDF04: 0F 28 CA - movaps xmm1,xmm2 GameAssembly.dll+9BDF07: F3 0F 5C 0D 99 7A F0 02 - subss xmm1,[GameAssembly.dll+38C59A8] // ---------- INJECTING HERE ---------- GameAssembly.dll+9BDF0F: F3 0F 11 43 18 - movss [rbx+18],xmm0 // ---------- DONE INJECTING ---------- GameAssembly.dll+9BDF14: 0F 2F C1 - comiss xmm0,xmm1 GameAssembly.dll+9BDF17: 73 17 - jae GameAssembly.dll+9BDF30 GameAssembly.dll+9BDF19: F3 0F 5C 15 27 7B F0 02 - subss xmm2,[GameAssembly.dll+38C5A48] GameAssembly.dll+9BDF21: 0F 2F C2 - comiss xmm0,xmm2 GameAssembly.dll+9BDF24: 72 39 - jb GameAssembly.dll+9BDF5F } </AssemblerScript> </CheatEntry> <CheatEntry> <ID>34</ID> <Description>"无限黄球"</Description> <Options moManualExpandCollapse="1"/> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>// Game Exe文件名 : oriandthewillofthewisps-pc.exe // Author : laoz // Exe 文件版本 : 2018.4.11.45208 // Module Version : // Script Date : 2022-05-14 // Created with : customAOBInjectionTemplates version: 1.3.9 [ENABLE] //注入点位置是xxxxxx指令。该指令是对xxxxxx进行查找什么改变这个地址操作得到的。 aobscanmodule(aob_HuangQiuZhiZhen,GameAssembly.dll,8B 40 30 48 83 C4 48 C3 E8 CA) registersymbol(aob_HuangQiuZhiZhen) //这里HuangQiuZhiZhen的意思是:黄球指针 alloc(newmem_HuangQiuZhiZhen,256,GameAssembly.dll) label(return_HuangQiuZhiZhen) //以下人造指针1 alloc(HuangQiuZhiZhen_P,8) //人造指针8或4字节(64位需要8字节) registersymbol(HuangQiuZhiZhen_P) // //以上人造指针1 //以下人造指针2 alloc(HuangQiuZhiZhen_P_xx2,8) //人造指针,xx2可自己修改为HP或子弹等 registersymbol(HuangQiuZhiZhen_P_xx2) // //以上人造指针2 newmem_HuangQiuZhiZhen: //以下进行人造指针------------------------------------------------ //以上------------------------------------------------ //下面放置新增代码 //------------------------------------------------------------------- mov [HuangQiuZhiZhen_P],rax //------------------------------------------------------------------- //以下为原代码 mov eax,[rax+30] add rsp,48 jmp return_HuangQiuZhiZhen aob_HuangQiuZhiZhen: jmp newmem_HuangQiuZhiZhen nop 2 return_HuangQiuZhiZhen: [DISABLE] aob_HuangQiuZhiZhen: db 8B 40 30 48 83 C4 48 unregistersymbol(*) dealloc(*) { // ORIGINAL CODE - INJECTION POINT: GameAssembly.dll+901AB9 GameAssembly.dll+901AAE: 74 23 - je GameAssembly.dll+901AD3 GameAssembly.dll+901AB0: 48 8B 40 18 - mov rax,[rax+18] GameAssembly.dll+901AB4: 48 85 C0 - test rax,rax GameAssembly.dll+901AB7: 74 14 - je GameAssembly.dll+901ACD // ---------- INJECTING HERE ---------- GameAssembly.dll+901AB9: 8B 40 30 - mov eax,[rax+30] // ---------- DONE INJECTING ---------- GameAssembly.dll+901ABC: 48 83 C4 48 - add rsp,48 GameAssembly.dll+901AC0: C3 - ret GameAssembly.dll+901AC1: E8 CA C5 96 FF - call GameAssembly.il2cpp_custom_attrs_construct+EE40 GameAssembly.dll+901AC6: CC - int 3 GameAssembly.dll+901AC7: E8 C4 C5 96 FF - call GameAssembly.il2cpp_custom_attrs_construct+EE40 GameAssembly.dll+901ACC: CC - int 3 } </AssemblerScript> <CheatEntries> <CheatEntry> <ID>35</ID> <Description>"黄球经验值"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>HuangQiuZhiZhen_P</Address> <Offsets> <Offset>30</Offset> </Offsets> </CheatEntry> </CheatEntries> </CheatEntry> <CheatEntry> <ID>185</ID> <Description>"无限氧气--学会潜水前用"</Description> <Options moAlwaysHideChildren="1" moManualExpandCollapse="1"/> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>// Game Exe文件名 : oriandthewillofthewisps-pc.exe // Author : laoz // Exe 文件版本 : 2018.4.11.45208 // Module Version : // Script Date : 2022-05-14 // Created with : customAOBInjectionTemplates version: 1.3.9 [ENABLE] //注入点位置是xxxxxx指令。该指令是对xxxxxx进行查找什么改变这个地址操作得到的。 aobscanmodule(aob_YangQiO2,GameAssembly.dll,F3 0F 11 B3 64 03 00 00) registersymbol(aob_YangQiO2) //这里YangQiO2的意思是:氧气o2 alloc(newmem_YangQiO2,256,GameAssembly.dll) label(return_YangQiO2) //以下人造指针1 alloc(YangQiO2_P_xx1,8) //人造指针8或4字节(64位需要8字节) registersymbol(YangQiO2_P_xx1) // //以上人造指针1 //以下人造指针2 alloc(YangQiO2_P_xx2,8) //人造指针,xx2可自己修改为HP或子弹等 registersymbol(YangQiO2_P_xx2) // //以上人造指针2 newmem_YangQiO2: //以下进行人造指针------------------------------------------------ mov [YangQiO2_P_xx1],rbx //以上进行人造指针------------------------------------------------ //下面放置新增代码 //------------------------------------------------------------------- mov [rbx+00000364],(float)16 //------------------------------------------------------------------- //以下为原代码 //movss [rbx+00000364],xmm6 jmp return_YangQiO2 aob_YangQiO2: jmp newmem_YangQiO2 nop 3 return_YangQiO2: [DISABLE] aob_YangQiO2: db F3 0F 11 B3 64 03 00 00 unregistersymbol(*) dealloc(*) { // ORIGINAL CODE - INJECTION POINT: GameAssembly.dll.il2cpp+9BA162 GameAssembly.dll.il2cpp+9BA14B: 83 B9 D8 00 00 00 00 - cmp dword ptr [rcx+000000D8],00 GameAssembly.dll.il2cpp+9BA152: 75 05 - jne GameAssembly.dll.il2cpp+9BA159 GameAssembly.dll.il2cpp+9BA154: E8 A7 A9 5B FF - call GameAssembly.dll.text+24CB00 GameAssembly.dll.il2cpp+9BA159: F3 0F 5C F7 - subss xmm6,xmm7 GameAssembly.dll.il2cpp+9BA15D: F3 41 0F 5F F0 - maxss xmm6,xmm8 // ---------- INJECTING HERE ---------- GameAssembly.dll.il2cpp+9BA162: F3 0F 11 B3 64 03 00 00 - movss [rbx+00000364],xmm6 // ---------- DONE INJECTING ---------- GameAssembly.dll.il2cpp+9BA16A: 41 0F 2E F0 - ucomiss xmm6,xmm8 GameAssembly.dll.il2cpp+9BA16E: 0F 8A AF 03 00 00 - jp GameAssembly.dll.il2cpp+9BA523 GameAssembly.dll.il2cpp+9BA174: 0F 85 A9 03 00 00 - jne GameAssembly.dll.il2cpp+9BA523 GameAssembly.dll.il2cpp+9BA17A: 80 BB E8 00 00 00 00 - cmp byte ptr [rbx+000000E8],00 GameAssembly.dll.il2cpp+9BA181: 0F 85 4D 01 00 00 - jne GameAssembly.dll.il2cpp+9BA2D4 GameAssembly.dll.il2cpp+9BA187: F3 0F 10 83 48 03 00 00 - movss xmm0,[rbx+00000348] } </AssemblerScript> <CheatEntries> <CheatEntry> <ID>184</ID> <Description>"氧气"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>YangQiO2_P_xx1</Address> <Offsets> <Offset>364</Offset> </Offsets> <CheatEntries> <CheatEntry> <ID>201</ID> <Description>"氧气指针扫描结果"</Description> <Options moAlwaysHideChildren="1" moManualExpandCollapse="1"/> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+04368828</Address> <Offsets> <Offset>364</Offset> <Offset>A0</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>B8</Offset> </Offsets> <CheatEntries> <CheatEntry> <ID>204</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+0437B130</Address> <Offsets> <Offset>364</Offset> <Offset>A0</Offset> <Offset>28</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> </CheatEntries> </CheatEntry> </CheatEntries> </CheatEntry> </CheatEntries> </CheatEntry> <CheatEntry> <ID>90</ID> <Description>"无限矿石--此脚本不要写入矿石,否则崩溃"</Description> <Options moManualExpandCollapse="1"/> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>// Game Exe文件名 : oriandthewillofthewisps-pc.exe // Author : laoz // Exe 文件版本 : 2018.4.11.45208 // Module Version : // Script Date : 2022-05-17 // Created with : customAOBInjectionTemplates version: 1.3.9 [ENABLE] //注入点位置是频繁访问矿石的指令。该指令是对xxxxxx进行查找什么改变这个地址操作得到的。 //注意,本脚本仅在与格鲁姆交谈建设项目时候有效。 aobscanmodule(aob_KuangShi,GameAssembly.dll,8B 40 34 48 83 C4 48 C3 E8 3A) registersymbol(aob_KuangShi) //这里KuangShi的意思是:矿石 alloc(newmem_KuangShi,256,GameAssembly.dll) label(return_KuangShi) //以下人造指针1 alloc(KuangShi_P_xx1,8) //人造指针8或4字节(64位需要8字节) registersymbol(KuangShi_P_xx1) // //以上人造指针1 //以下人造指针2 alloc(KuangShi_P_xx2,8) //人造指针,xx2可自己修改为HP或子弹等 registersymbol(KuangShi_P_xx2) // //以上人造指针2 newmem_KuangShi: //以下进行人造指针------------------------------------------------ mov [KuangShi_P_xx1],rax //以上进行人造指针------------------------------------------------ //下面放置新增代码 //------------------------------------------------------------------- //------------------------------------------------------------------- //以下为原代码 mov eax,[rax+34] add rsp,48 jmp return_KuangShi aob_KuangShi: jmp newmem_KuangShi nop 2 return_KuangShi: [DISABLE] aob_KuangShi: db 8B 40 34 48 83 C4 48 unregistersymbol(*) dealloc(*) { // ORIGINAL CODE - INJECTION POINT: GameAssembly.dll+901C49 GameAssembly.dll+901C36: E8 05 D3 B2 00 - call GameAssembly.dll+142EF40 GameAssembly.dll+901C3B: 48 85 C0 - test rax,rax GameAssembly.dll+901C3E: 74 23 - je GameAssembly.dll+901C63 GameAssembly.dll+901C40: 48 8B 40 18 - mov rax,[rax+18] GameAssembly.dll+901C44: 48 85 C0 - test rax,rax GameAssembly.dll+901C47: 74 14 - je GameAssembly.dll+901C5D // ---------- INJECTING HERE ---------- GameAssembly.dll+901C49: 8B 40 34 - mov eax,[rax+34] // ---------- DONE INJECTING ---------- GameAssembly.dll+901C4C: 48 83 C4 48 - add rsp,48 GameAssembly.dll+901C50: C3 - ret } </AssemblerScript> <CheatEntries> <CheatEntry> <ID>88</ID> <Description>"矿石"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>KuangShi_P_xx1</Address> <Offsets> <Offset>34</Offset> </Offsets> </CheatEntry> </CheatEntries> </CheatEntry> <CheatEntry> <ID>305</ID> <Description>"无限开门钥匙碎片"</Description> <Options moAlwaysHideChildren="1" moManualExpandCollapse="1"/> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>// Game Exe文件名 : oriandthewillofthewisps-pc.exe // Author : laoz // Exe 文件版本 : 2018.4.11.45208 // Module Version : // Script Date : 2022-05-24 // Created with : customAOBInjectionTemplates version: 1.3.9 [ENABLE] //注入点位置是频繁读取开门钥匙碎片地址的指令。本位置是对地址“ 查找什么改写这个地址”得到。 aobscanmodule(aob_KaiMenYaoShiPian,GameAssembly.dll,8B 40 28 48 83 C4 48 C3 E8 8A) registersymbol(aob_KaiMenYaoShiPian) //KaiMenYaoShiPian ==拼音:开门钥匙片 alloc(newmem_KaiMenYaoShiPian,256,GameAssembly.dll) label(return_KaiMenYaoShiPian) label(KaiMenYaoShiPian_YDM) //原始代码 //以下人造指针1 alloc(KaiMenYaoShiPian_P_1,8) //人造指针8或4字节(64位需要8字节) registersymbol(KaiMenYaoShiPian_P_1) //人造指针,存放??地址 //以上人造指针1 //以下人造指针2 alloc(KaiMenYaoShiPian_P_2,8) //人造指针,存放??地址 registersymbol(KaiMenYaoShiPian_P_2) // //以上人造指针2 //以下申请内存 alloc(KaiMenYaoShiPian_Mem_1,8) //申请的内存4或8字节,用来存放??值 registersymbol(KaiMenYaoShiPian_Mem_1) // //以上申请内存 newmem_KaiMenYaoShiPian: //以下进行人造指针------------------------------------------------ mov [KaiMenYaoShiPian_P_1],rax //开门钥匙碎片指针+28 //以上进行人造指针------------------------------------------------ //下面放置新增代码 //---------------------------------------------------------------- mov [rax+28],#99 //给99个钥匙碎片 //---------------------------------------------------------------- KaiMenYaoShiPian_YDM: //原始代码 //以下为原代码—————————————————————————— mov eax,[rax+28] add rsp,48 jmp return_KaiMenYaoShiPian aob_KaiMenYaoShiPian: jmp newmem_KaiMenYaoShiPian nop 2 return_KaiMenYaoShiPian: [DISABLE] aob_KaiMenYaoShiPian: db 8B 40 28 48 83 C4 48 unregistersymbol(*) dealloc(*) { // ORIGINAL CODE - INJECTION POINT: GameAssembly.dll+8F4CF9 GameAssembly.dll+8F4C7D: 48 63 88 C0 00 00 00 - movsxd rcx,dword ptr [rax+000000C0] GameAssembly.dll+8F4C84: 48 8B 05 E5 E7 AE 03 - mov rax,[GameAssembly.dll+43E3470] GameAssembly.dll+8F4C8B: 33 D2 - xor edx,edx GameAssembly.dll+8F4C8D: 48 89 54 24 28 - mov [rsp+28],rdx GameAssembly.dll+8F4C92: 48 89 54 24 30 - mov [rsp+30],rdx GameAssembly.dll+8F4C97: 48 89 54 24 38 - mov [rsp+38],rdx GameAssembly.dll+8F4C9C: 4C 8D 44 24 28 - lea r8,[rsp+28] GameAssembly.dll+8F4CA1: 8B 94 01 24 ED 06 00 - mov edx,[rcx+rax+0006ED24] GameAssembly.dll+8F4CA8: 8B 8C 01 20 ED 06 00 - mov ecx,[rcx+rax+0006ED20] GameAssembly.dll+8F4CAF: E8 8C 62 94 FF - call GameAssembly.il2cpp_class_is_interface+5670 GameAssembly.dll+8F4CB4: 90 - nop GameAssembly.dll+8F4CB5: 33 C9 - xor ecx,ecx GameAssembly.dll+8F4CB7: FF 15 0B 52 9F 03 - call qword ptr [GameAssembly.dll+42E9EC8] GameAssembly.dll+8F4CBD: 90 - nop GameAssembly.dll+8F4CBE: C6 05 31 1B AF 03 01 - mov byte ptr [GameAssembly.dll+43E67F6],01 GameAssembly.dll+8F4CC5: 48 8B 05 9C 84 A9 03 - mov rax,[GameAssembly.dll+438D168] GameAssembly.dll+8F4CCC: 48 8B 88 B8 00 00 00 - mov rcx,[rax+000000B8] GameAssembly.dll+8F4CD3: 48 8B 01 - mov rax,[rcx] GameAssembly.dll+8F4CD6: 48 85 C0 - test rax,rax GameAssembly.dll+8F4CD9: 74 2C - je GameAssembly.dll+8F4D07 GameAssembly.dll+8F4CDB: 48 8B 48 18 - mov rcx,[rax+18] GameAssembly.dll+8F4CDF: 48 85 C9 - test rcx,rcx GameAssembly.dll+8F4CE2: 74 1D - je GameAssembly.dll+8F4D01 GameAssembly.dll+8F4CE4: 33 D2 - xor edx,edx GameAssembly.dll+8F4CE6: E8 55 A2 B3 00 - call GameAssembly.dll+142EF40 GameAssembly.dll+8F4CEB: 48 85 C0 - test rax,rax GameAssembly.dll+8F4CEE: 74 23 - je GameAssembly.dll+8F4D13 GameAssembly.dll+8F4CF0: 48 8B 40 18 - mov rax,[rax+18] GameAssembly.dll+8F4CF4: 48 85 C0 - test rax,rax GameAssembly.dll+8F4CF7: 74 14 - je GameAssembly.dll+8F4D0D // ---------- INJECTING HERE ---------- GameAssembly.dll+8F4CF9: 8B 40 28 - mov eax,[rax+28] // ---------- DONE INJECTING ---------- GameAssembly.dll+8F4CFC: 48 83 C4 48 - add rsp,48 GameAssembly.dll+8F4D00: C3 - ret GameAssembly.dll+8F4D01: E8 8A 93 97 FF - call GameAssembly.il2cpp_custom_attrs_construct+EE40 GameAssembly.dll+8F4D06: CC - int 3 GameAssembly.dll+8F4D07: E8 84 93 97 FF - call GameAssembly.il2cpp_custom_attrs_construct+EE40 GameAssembly.dll+8F4D0C: CC - int 3 GameAssembly.dll+8F4D0D: E8 7E 93 97 FF - call GameAssembly.il2cpp_custom_attrs_construct+EE40 GameAssembly.dll+8F4D12: CC - int 3 GameAssembly.dll+8F4D13: E8 78 93 97 FF - call GameAssembly.il2cpp_custom_attrs_construct+EE40 GameAssembly.dll+8F4D18: CC - int 3 GameAssembly.dll+8F4D19: CC - int 3 GameAssembly.dll+8F4D1A: CC - int 3 GameAssembly.dll+8F4D1B: CC - int 3 GameAssembly.dll+8F4D1C: CC - int 3 GameAssembly.dll+8F4D1D: CC - int 3 GameAssembly.dll+8F4D1E: CC - int 3 GameAssembly.dll+8F4D1F: CC - int 3 GameAssembly.dll+8F4D20: 40 53 - push rbx GameAssembly.dll+8F4D22: 48 83 EC 40 - sub rsp,40 GameAssembly.dll+8F4D26: 48 C7 44 24 20 FE FF FF FF - mov qword ptr [rsp+20],FFFFFFFFFFFFFFFE GameAssembly.dll+8F4D2F: 8B DA - mov ebx,edx GameAssembly.dll+8F4D31: 80 3D E6 1A AF 03 00 - cmp byte ptr [GameAssembly.dll+43E681E],00 GameAssembly.dll+8F4D38: 75 4F - jne GameAssembly.dll+8F4D89 GameAssembly.dll+8F4D3A: 48 8B 05 3F E7 AE 03 - mov rax,[GameAssembly.dll+43E3480] GameAssembly.dll+8F4D41: 48 63 88 C0 00 00 00 - movsxd rcx,dword ptr [rax+000000C0] GameAssembly.dll+8F4D48: 48 8B 05 21 E7 AE 03 - mov rax,[GameAssembly.dll+43E3470] GameAssembly.dll+8F4D4F: 33 D2 - xor edx,edx GameAssembly.dll+8F4D51: 48 89 54 24 28 - mov [rsp+28],rdx GameAssembly.dll+8F4D56: 48 89 54 24 30 - mov [rsp+30],rdx GameAssembly.dll+8F4D5B: 48 89 54 24 38 - mov [rsp+38],rdx } </AssemblerScript> <CheatEntries> <CheatEntry> <ID>303</ID> <Description>"钥匙碎片"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>KaiMenYaoShiPian_P_1</Address> <Offsets> <Offset>28</Offset> </Offsets> </CheatEntry> </CheatEntries> </CheatEntry> <CheatEntry> <ID>293</ID> <Description>"猫头鹰无限跳--可自定义跳跃次数(初始4连跳)"</Description> <Options moManualExpandCollapse="1"/> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>// Game Exe文件名 : oriandthewillofthewisps-pc.exe // Author : laoz // Exe 文件版本 : 2018.4.11.45208 // Module Version : // Script Date : 2022-05-21 // Created with : customAOBInjectionTemplates version: 1.3.9 [ENABLE] //注入点位置是频繁读取猫头鹰跳跃次数地址的指令。 aobscanmodule(aob_MaoTouYingJump,GameAssembly.dll,FF 89 43 64 48 83 C4 40) registersymbol(aob_MaoTouYingJump) //这里MaoTouYingJump的意思是:猫头鹰跳 alloc(newmem_MaoTouYingJump,256,GameAssembly.dll) label(return_MaoTouYingJump) //以下人造指针1 alloc(MaoTouYingJump_P,8) //人造指针8或4字节(64位需要8字节) registersymbol(MaoTouYingJump_P) // //以上人造指针1 //以下存放自定义的猫头鹰的跳跃次数 alloc(MaoTouYingJump_CiShu,4) //猫头鹰跳次数 registersymbol(MaoTouYingJump_CiShu) // //以上 newmem_MaoTouYingJump: //以下进行人造指针------------------------------------------------ mov [MaoTouYingJump_P],rbx //以上进行人造指针------------------------------------------------ //下面放置新增代码 //------------------------------------------------------------------- cmp [MaoTouYingJump_CiShu],0 //比较存放跳跃次数的内存是否0 jnz MaoTouYingJump_YDM //不为0,则跳到原代码执行 mov [MaoTouYingJump_CiShu],3 //为0,则将4连跳写入地址.用户可以在CT表中手动改 MaoTouYingJump_YDM: mov eax,[MaoTouYingJump_CiShu] //存放跳跃次数的内存不为0,说明有用户手工改写的次数 //------------------------------------------------------------------- //以下为原代码 mov [rbx+64],eax add rsp,40 jmp return_MaoTouYingJump aob_MaoTouYingJump+01: jmp newmem_MaoTouYingJump nop 2 return_MaoTouYingJump: [DISABLE] aob_MaoTouYingJump+01: db 89 43 64 48 83 C4 40 unregistersymbol(*) dealloc(*) { // ORIGINAL CODE - INJECTION POINT: GameAssembly.dll+AE5090 GameAssembly.dll+AE5089: 33 C9 - xor ecx,ecx GameAssembly.dll+AE508B: E8 80 3E E8 FF - call GameAssembly.dll+968F10 // ---------- INJECTING HERE ---------- GameAssembly.dll+AE5090: 89 43 64 - mov [rbx+64],eax // ---------- DONE INJECTING ---------- GameAssembly.dll+AE5093: 48 83 C4 40 - add rsp,40 GameAssembly.dll+AE5097: 5B - pop rbx GameAssembly.dll+AE5098: C3 - ret } </AssemblerScript> <CheatEntries> <CheatEntry> <ID>294</ID> <Description>"跳越次数-初始4,可手工改"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>MaoTouYingJump_CiShu</Address> </CheatEntry> <CheatEntry> <ID>292</ID> <Description>"原始跳跃次数"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>MaoTouYingJump_P</Address> <Offsets> <Offset>64</Offset> </Offsets> </CheatEntry> </CheatEntries> </CheatEntry> </CheatEntries> </CheatEntry> <CheatEntry> <ID>69</ID> <Description>"=======Ori2-游戏作弊脚本可全开================================"</Description> <Options moManualExpandCollapse="1" moActivateChildrenAsWell="1" moDeactivateChildrenAsWell="1"/> <Color>0000FF</Color> <GroupHeader>1</GroupHeader> <CheatEntries> <CheatEntry> <ID>161</ID> <Description>"无限HP(小20则加)+无限能量(小3则加)"</Description> <Options moAlwaysHideChildren="1" moManualExpandCollapse="1"/> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>// Game Exe文件名 : oriandthewillofthewisps-pc.exe // Author : laoz // Exe 文件版本 : 2018.4.11.45208 // Module Version : // Script Date : 2022-05-19 // Created with : customAOBInjectionTemplates version: 1.3.9 [ENABLE] //注入点位置是唯一的频繁读HP地址的指令。 aobscanmodule(aob_PinFanDuHP,GameAssembly.dll,8B 40 10 89 43 2C C6) registersymbol(aob_PinFanDuHP) //这里PinFanDuHP的意思是:频繁读HP alloc(newmem_PinFanDuHP,256,GameAssembly.dll) label(return_PinFanDuHP) //以下人造指针1 alloc(PinFanDuHP_P,8) //人造指针8或4字节(64位需要8字节) registersymbol(PinFanDuHP_P) //频繁读HP //以上人造指针1 label(return_PinFanDuHP_YDM) //频繁读HP_原始代码 label(return_PinFanDuHP_NengLiang) //频繁读HP_能量,判断能量是否应该增加 //以下人造指针2 alloc(PinFanDuHP_P_temp,8) //人造指针,xx2可自己修改为HP或子弹等 registersymbol(PinFanDuHP_P_temp) // //以上人造指针2 newmem_PinFanDuHP: //以下进行人造指针------------------------------------------------ mov [PinFanDuHP_P],rax //以上进行人造指针------------------------------------------------ //下面放置新增代码 //------------------------------------------------------------------- cmp [rax+10],(float)20 //奥日HP的值和20比较 //HP大于或等于20跳转到:return_PinFanDuHP_YDM: //原代码 jae return_PinFanDuHP_NengLiang //跳到判断能量是否该增加标签 //小于20则执行以下指令,给HP加到当前最大值 push rdx //保护edx,因要用edx中转(因为mov不能内存到内存)。 mov edx,[rax+14] //rax+14存放HP最大值,但是是4字节值,须转为浮点数 cvtsi2ss XMM15,edx //将m32转为32位单浮点数! 放到xmm15的第一位置 movss [PinFanDuHP_P_temp],xmm15 //将浮点数存入内存地址中转 mov edx,[PinFanDuHP_P_temp] //将中转内存地址值用edx中转 mov [rax+10],edx pop rdx //------------------------------------------------------------------- return_PinFanDuHP_NengLiang: cmp [rax+18],(float)3 //奥日能量值和3比较,也就是3个绿球 //大于或等于3个球跳转到:return_PinFanDuHP_YDM: //原代码 jae return_PinFanDuHP_YDM //原代码 //小于3则执行以下指令,给能量值加到当前最大值 //mov [rbx+10],(float)100 //下面的语句其实简单就这一句 push rdx //保护edx,因要用edx中转(因为mov不能内存到内存)。 mov edx,[rax+1C] //rax+1C存放能量最大值 mov [rax+18],edx pop rdx return_PinFanDuHP_YDM: //原代码 //------------------------------------------------------------------- //以下为原代码 mov eax,[rax+10] mov [rbx+2C],eax jmp return_PinFanDuHP aob_PinFanDuHP: jmp newmem_PinFanDuHP nop return_PinFanDuHP: [DISABLE] aob_PinFanDuHP: db 8B 40 10 89 43 2C unregistersymbol(*) dealloc(*) { // ORIGINAL CODE - INJECTION POINT: GameAssembly.dll+F141D5 GameAssembly.dll+F141BE: 74 2A - je GameAssembly.dll+F141EA GameAssembly.dll+F141C0: 33 D2 - xor edx,edx GameAssembly.dll+F141C2: E8 79 AD 51 00 - call GameAssembly.dll+142EF40 GameAssembly.dll+F141C7: 48 85 C0 - test rax,rax GameAssembly.dll+F141CA: 74 30 - je GameAssembly.dll+F141FC GameAssembly.dll+F141CC: 48 8B 40 28 - mov rax,[rax+28] GameAssembly.dll+F141D0: 48 85 C0 - test rax,rax GameAssembly.dll+F141D3: 74 21 - je GameAssembly.dll+F141F6 // ---------- INJECTING HERE ---------- GameAssembly.dll+F141D5: 8B 40 10 - mov eax,[rax+10] // ---------- DONE INJECTING ---------- GameAssembly.dll+F141D8: 89 43 2C - mov [rbx+2C],eax GameAssembly.dll+F141DB: C6 43 28 00 - mov byte ptr [rbx+28],00 GameAssembly.dll+F141DF: F3 0F 10 43 2C - movss xmm0,[rbx+2C] GameAssembly.dll+F141E4: 48 83 C4 40 - add rsp,40 GameAssembly.dll+F141E8: 5B - pop rbx GameAssembly.dll+F141E9: C3 - ret } </AssemblerScript> <CheatEntries> <CheatEntry> <ID>162</ID> <Description>"能量当前上限"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>PinFanDuHP_P</Address> <Offsets> <Offset>1C</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>163</ID> <Description>"能量-1个球是浮点1"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>PinFanDuHP_P</Address> <Offsets> <Offset>18</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>164</ID> <Description>"HP当前上限"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>PinFanDuHP_P</Address> <Offsets> <Offset>14</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>165</ID> <Description>"HP-1个球是浮点10"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>PinFanDuHP_P</Address> <Offsets> <Offset>10</Offset> </Offsets> <CheatEntries> <CheatEntry> <ID>166</ID> <Description>"HP指针扫描结果"</Description> <Options moAlwaysHideChildren="1" moManualExpandCollapse="1"/> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+04383FC0</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>18</Offset> <Offset>20</Offset> <Offset>B8</Offset> </Offsets> <CheatEntries> <CheatEntry> <ID>167</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+043BB910</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>18</Offset> <Offset>10</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>168</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+0438D168</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>18</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>169</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+04392510</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>38</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>170</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+043D6F00</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>38</Offset> <Offset>30</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>171</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+0438F680</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>38</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>172</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+0435B2D8</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>48</Offset> <Offset>20</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>173</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+043B7A68</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>48</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>174</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+043870F0</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>88</Offset> <Offset>30</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>175</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+04353068</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>88</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>176</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+0438D5E8</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>D8</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>177</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+04383BA0</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>D8</Offset> <Offset>100</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>178</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+04354850</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>D8</Offset> <Offset>C0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>179</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+043BD470</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>D8</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>180</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+0439A960</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>128</Offset> <Offset>8</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>181</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+0438E6C0</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>128</Offset> <Offset>C8</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>182</ID> <Description>"指针扫描结果"</Description> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+043ABD70</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>128</Offset> <Offset>128</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>183</ID> <Description>"指针扫描结果"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>"GameAssembly.dll"+043D70A0</Address> <Offsets> <Offset>10</Offset> <Offset>28</Offset> <Offset>30</Offset> <Offset>178</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> </CheatEntries> </CheatEntry> </CheatEntries> </CheatEntry> </CheatEntries> </CheatEntry> <CheatEntry> <ID>126</ID> <Description>"一击必杀!"</Description> <Options moAlwaysHideChildren="1" moManualExpandCollapse="1"/> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>// Game Exe文件名 : oriandthewillofthewisps-pc.exe// Exe文件版本: 2018.4.11.45208 // Author : laoz // Script Date : 2022-05-14 // Created with : customAOBInjectionTemplates version: 1.3.9 [ENABLE] {注入点位置:找到敌人HP地址,对该地址找“ 什么写入这个地址”,找到: GameAssembly.dll+B612E0 - F3 0F11 73 28 - movss [rbx+28],xmm6 这句指令后面就是pop和ret指令,因此步出到上一层如下: 《一》GameAssembly.dll+B63FEA - F3 0F5C CA - subss xmm1,xmm2 《二》GameAssembly.dll+B63FEE - 4C 8B 80 80020000 - mov r8,[rax+00000280] 《三》GameAssembly.dll+B63FF5 - 48 8B CF - mov rcx,rdi 《四》GameAssembly.dll+B63FF8 - FF 90 78020000 - call qword ptr [rax+00000278] 《五》GameAssembly.dll+B63FFE - 4C 8B 77 48 - mov r14,[rdi+48] 步出返回的是《五》这句。而写敌HP指令在《四》这个call中。 向上看《一》这句指令,明显是减操作。且xmm1是敌HP值,xmm2是攻击值。 因此本脚本从《一》指令进行注入。 } aobscanmodule(aob_YiJiBiShaA,GameAssembly.dll,F3 0F 5C CA 4C 8B 80 80 02 00 00) registersymbol(aob_YiJiBiShaA) //YiJiBiShaA是:一击必杀 alloc(newmem_YiJiBiShaA,256,GameAssembly.dll) label(return_YiJiBiShaA) //以下为攻击方式判断标志位-1脚本大值99999攻击,0为0攻击,-1为原始攻击值 alloc(YiJiBiShaA_P_BiaoZhi,8) //选择攻击方式判断标志位 registersymbol(YiJiBiShaA_P_BiaoZhi) // //以上为攻击方式判断标志位 label(YiJiBiShaA_Zheng1) //正1,代表设置攻击值99999 label(YiJiBiShaA_Fu1) //负1,代表设置攻击值为原值 label(YiJiBiShaA_0) //0, 代表设置攻击值0。可用于观察敌HP情况。 label(YiJiBiShaA_YuanDaiMa)//原始代码 //以下临时空间 alloc(YiJiBiShaA_temp,4) //人造指针8或4字节(64位需要8字节) registersymbol(YiJiBiShaA_temp) // //以上临时空间 //以下人造指针2 alloc(YiJiBiShaA_P_xx2,4) //人造指针,存实际攻击值 registersymbol(YiJiBiShaA_P_xx2) // //以上人造指针2 //以下人造指针3 alloc(YiJiBiShaA_P_xx3,8) //人造指针,敌人的HP registersymbol(YiJiBiShaA_P_xx3) // //以上人造指针3 YiJiBiShaA_P_BiaoZhi: //运行脚本先将攻击模式初始设定为1,暨使用99999攻击值 db 1 YiJiBiShaA_temp: //运行脚本先将攻击值初始设定为99999 db 80 4F C3 47 //浮点99999的十六进制表示为:47C34F80,写入内存须倒序 newmem_YiJiBiShaA: //以下进行人造指针------------------------------------------------ movss [YiJiBiShaA_P_xx2],xmm2 //实际的攻击值 mov [YiJiBiShaA_P_xx3],rdi //rdi+28为敌HP地址 //以上进行人造指针------------------------------------------------ //下面放置新增代码 //------------------------------------------------------------------- push r14 //内存中转使用此r14寄存器,先保护。例如:不能直接从寄存器到浮点寄存器。 cmp byte ptr [YiJiBiShaA_P_BiaoZhi],0 //判断攻击方式是否为0 je YiJiBiShaA_0 //则跳到下面进行攻击方式0 cmp byte ptr [YiJiBiShaA_P_BiaoZhi],1 //判断攻击方式是否为1 je YiJiBiShaA_Zheng1 //则跳到下面进行攻击方式1 cmp byte ptr [YiJiBiShaA_P_BiaoZhi],-1 //判断攻击方式是否为-1 je YiJiBiShaA_Fu1 //则跳到下面进行攻击方式-1 //--------攻击方式1:脚本赋大值99999攻击 YiJiBiShaA_Zheng1: //正1,将要初始设置攻击值99999 //mov r14,(float)99999 //攻击值99999放到r14 //mov [YiJiBiShaA_temp],r14 //从r14中转到临时地址,这个可做为巨大攻击值指针 pop r14 movss xmm2,[YiJiBiShaA_temp]//从临时地址到xmm2 jmp YiJiBiShaA_YuanDaiMa //--------攻击方式0:攻击值设置为0 YiJiBiShaA_0://0,代表将要设置攻击值0。 mov r14,(float)0 //攻击值0放到r14 mov [YiJiBiShaA_temp],r14 //从r14中转到临时地址,这个可做为巨大攻击值指针 pop r14 movss xmm2,[YiJiBiShaA_temp]//从临时地址到xmm2 jmp YiJiBiShaA_YuanDaiMa //--------攻击方式-1:用游戏原始攻击值 YiJiBiShaA_Fu1://负1,代表设置攻击值为原值 pop r14 jmp YiJiBiShaA_YuanDaiMa YiJiBiShaA_YuanDaiMa: //以下为原代码 subss xmm1,xmm2 mov r8,[rax+00000280] jmp return_YiJiBiShaA aob_YiJiBiShaA: jmp newmem_YiJiBiShaA nop 6 return_YiJiBiShaA: [DISABLE] aob_YiJiBiShaA: db F3 0F 5C CA 4C 8B 80 80 02 00 00 unregistersymbol(*) dealloc(*) { // ORIGINAL CODE - INJECTION POINT: GameAssembly.dll+B63FEA GameAssembly.dll+B63FDE: 48 8B 07 - mov rax,[rdi] GameAssembly.dll+B63FE1: F3 0F 10 4F 28 - movss xmm1,[rdi+28] GameAssembly.dll+B63FE6: 0F C6 D2 AA - shufps xmm2,xmm2,-56 // ---------- INJECTING HERE ---------- GameAssembly.dll+B63FEA: F3 0F 5C CA - subss xmm1,xmm2 // ---------- DONE INJECTING ---------- GameAssembly.dll+B63FEE: 4C 8B 80 80 02 00 00 - mov r8,[rax+00000280] GameAssembly.dll+B63FF5: 48 8B CF - mov rcx,rdi GameAssembly.dll+B63FF8: FF 90 78 02 00 00 - call qword ptr [rax+00000278] GameAssembly.dll+B63FFE: 4C 8B 77 48 - mov r14,[rdi+48] } </AssemblerScript> <CheatEntries> <CheatEntry> <ID>96</ID> <Description>"标志:-1原始攻击,0为0攻击,1脚本攻击"</Description> <DropDownList ReadOnly="1" DescriptionOnly="1">1:攻击值设99999(可在下面手改) 0:攻击值设为0 -1:游戏原始攻击值 </DropDownList> <ShowAsSigned>1</ShowAsSigned> <VariableType>Byte</VariableType> <Address>YiJiBiShaA_P_BiaoZhi</Address> </CheatEntry> <CheatEntry> <ID>103</ID> <Description>"攻击值设99999(可手改)"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>YiJiBiShaA_temp</Address> </CheatEntry> <CheatEntry> <ID>104</ID> <Description>"实际攻击值"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>YiJiBiShaA_P_xx2</Address> </CheatEntry> <CheatEntry> <ID>124</ID> <Description>"敌当前HP"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>Float</VariableType> <Address>YiJiBiShaA_P_xx3</Address> <Offsets> <Offset>28</Offset> </Offsets> </CheatEntry> </CheatEntries> </CheatEntry> <CheatEntry> <ID>290</ID> <Description>"单箭速射!不占装备核心栏位"</Description> <Options moAlwaysHideChildren="1" moManualExpandCollapse="1"/> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>// Game Exe文件名 : oriandthewillofthewisps-pc.exe // Author : laoz // Exe 文件版本 : 2018.4.11.45208 // Module Version : // Script Date : 2022-05-21 // Created with : customAOBInjectionTemplates version: 1.3.9 [ENABLE] //注入点位置是xxxxxx指令。 aobscanmodule(aob_ZhuangBeiHeXin,GameAssembly.dll,89 51 1C 48 8B D9) registersymbol(aob_ZhuangBeiHeXin) //这里ZhuangBeiHeXin的意思是:装备核心 alloc(newmem_ZhuangBeiHeXin,256,GameAssembly.dll) label(return_ZhuangBeiHeXin) //以下人造指针1 alloc(ZhuangBeiHeXin_P_xx1,8) //人造指针8或4字节(64位需要8字节) registersymbol(ZhuangBeiHeXin_P_xx1) // //以上人造指针1 label(ZhuangBeiHeXin_YDM) //以下人造指针2 alloc(ZhuangBeiHeXin_P_xx2,8) //人造指针,xx2可自己修改为HP或子弹等 registersymbol(ZhuangBeiHeXin_P_xx2) // //以上人造指针2 newmem_ZhuangBeiHeXin: //以下进行人造指针------------------------------------------------ cmp [rcx+1C+24],0D jne ZhuangBeiHeXin_YDM mov [ZhuangBeiHeXin_P_xx1],rcx mov edx,A //游戏共有8个栏位,但是设置为第10个栏位也起作用,哈哈 //以上进行人造指针------------------------------------------------ //下面放置新增代码 //------------------------------------------------------------------- ZhuangBeiHeXin_YDM: //------------------------------------------------------------------- //以下为原代码 mov [rcx+1C],edx mov rbx,rcx jmp return_ZhuangBeiHeXin aob_ZhuangBeiHeXin: jmp newmem_ZhuangBeiHeXin nop return_ZhuangBeiHeXin: [DISABLE] aob_ZhuangBeiHeXin: db 89 51 1C 48 8B D9 unregistersymbol(*) dealloc(*) { // ORIGINAL CODE - INJECTION POINT: GameAssembly.dll+143A1A6 GameAssembly.dll+143A1A0: 40 53 - push rbx GameAssembly.dll+143A1A2: 48 83 EC 20 - sub rsp,20 // ---------- INJECTING HERE ---------- GameAssembly.dll+143A1A6: 89 51 1C - mov [rcx+1C],edx // ---------- DONE INJECTING ---------- GameAssembly.dll+143A1A9: 48 8B D9 - mov rbx,rcx GameAssembly.dll+143A1AC: 33 D2 - xor edx,edx GameAssembly.dll+143A1AE: E8 AD 00 00 00 - call GameAssembly.dll+143A260 GameAssembly.dll+143A1B3: 33 D2 - xor edx,edx GameAssembly.dll+143A1B5: 48 8B CB - mov rcx,rbx } </AssemblerScript> <CheatEntries> <CheatEntry> <ID>289</ID> <Description>"说明:按照或者卸载速射一次,即可配备速射且不占用核心栏位"</Description> <Color>FF8000</Color> <GroupHeader>1</GroupHeader> </CheatEntry> <CheatEntry> <ID>276</ID> <Description>"装或卸一次速射,可速射且不占栏位"</Description> <ShowAsHex>1</ShowAsHex> <ShowAsSigned>0</ShowAsSigned> <Color>FF8000</Color> <VariableType>4 Bytes</VariableType> <Address>ZhuangBeiHeXin_P_xx1</Address> <Offsets> <Offset>1C</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>278</ID> <Description>"单箭速射标志指针扫描结果"</Description> <Options moAlwaysHideChildren="1" moManualExpandCollapse="1"/> <ShowAsHex>1</ShowAsHex> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043B27A0</Address> <Offsets> <Offset>1C</Offset> <Offset>78</Offset> <Offset>20</Offset> <Offset>28</Offset> <Offset>48</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> <CheatEntries> <CheatEntry> <ID>279</ID> <Description>"指针扫描结果"</Description> <ShowAsHex>1</ShowAsHex> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043B27A0</Address> <Offsets> <Offset>1C</Offset> <Offset>108</Offset> <Offset>28</Offset> <Offset>28</Offset> <Offset>48</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>280</ID> <Description>"指针扫描结果"</Description> <ShowAsHex>1</ShowAsHex> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043B27A0</Address> <Offsets> <Offset>1C</Offset> <Offset>198</Offset> <Offset>30</Offset> <Offset>28</Offset> <Offset>48</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>281</ID> <Description>"指针扫描结果"</Description> <ShowAsHex>1</ShowAsHex> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043613B8</Address> <Offsets> <Offset>1C</Offset> <Offset>30</Offset> <Offset>40</Offset> <Offset>50</Offset> <Offset>A8</Offset> <Offset>8</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>282</ID> <Description>"指针扫描结果"</Description> <ShowAsHex>1</ShowAsHex> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043613B8</Address> <Offsets> <Offset>1C</Offset> <Offset>30</Offset> <Offset>10</Offset> <Offset>48</Offset> <Offset>A8</Offset> <Offset>8</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>283</ID> <Description>"指针扫描结果"</Description> <ShowAsHex>1</ShowAsHex> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043613B8</Address> <Offsets> <Offset>1C</Offset> <Offset>30</Offset> <Offset>40</Offset> <Offset>50</Offset> <Offset>A8</Offset> <Offset>10</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>284</ID> <Description>"指针扫描结果"</Description> <ShowAsHex>1</ShowAsHex> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043613B8</Address> <Offsets> <Offset>1C</Offset> <Offset>30</Offset> <Offset>10</Offset> <Offset>48</Offset> <Offset>A8</Offset> <Offset>10</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>285</ID> <Description>"指针扫描结果"</Description> <ShowAsHex>1</ShowAsHex> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043B40C8</Address> <Offsets> <Offset>1C</Offset> <Offset>30</Offset> <Offset>40</Offset> <Offset>50</Offset> <Offset>A8</Offset> <Offset>48</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>286</ID> <Description>"指针扫描结果"</Description> <ShowAsHex>1</ShowAsHex> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043B40C8</Address> <Offsets> <Offset>1C</Offset> <Offset>30</Offset> <Offset>10</Offset> <Offset>48</Offset> <Offset>A8</Offset> <Offset>48</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>287</ID> <Description>"指针扫描结果"</Description> <ShowAsHex>1</ShowAsHex> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043B40C8</Address> <Offsets> <Offset>1C</Offset> <Offset>30</Offset> <Offset>40</Offset> <Offset>50</Offset> <Offset>A8</Offset> <Offset>50</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>288</ID> <Description>"指针扫描结果"</Description> <ShowAsHex>1</ShowAsHex> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043B40C8</Address> <Offsets> <Offset>1C</Offset> <Offset>30</Offset> <Offset>10</Offset> <Offset>48</Offset> <Offset>A8</Offset> <Offset>50</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> </CheatEntries> </CheatEntry> <CheatEntry> <ID>222</ID> <Description>"五箭弓速射"</Description> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>// Game Exe文件名 : oriandthewillofthewisps-pc.exe // Author : laoz // Exe 文件版本 : 2018.4.11.45208 // Module Version : // Script Date : 2022-05-20 // Created with : customAOBInjectionTemplates version: 1.3.9 [ENABLE] //注入点位置是类似搜索超级连续跳找到地址,然后找到指令。 aobscanmodule(aob_GongJianSuShe,GameAssembly.dll,83 78 1C FF 0F 95 C0 48 83 C4 40) registersymbol(aob_GongJianSuShe) //这里GongJianSuShe的意思是:弓箭速射 alloc(newmem_GongJianSuShe,256,GameAssembly.dll) label(return_GongJianSuShe) newmem_GongJianSuShe: //以下进行人造指针------------------------------------------------ //以上进行人造指针------------------------------------------------ //下面放置新增代码 //------------------------------------------------------------------- //------------------------------------------------------------------- //以下为原代码 //cmp dword ptr [rax+1C],-01 //注销掉实现速射 setne al jmp return_GongJianSuShe aob_GongJianSuShe: jmp newmem_GongJianSuShe nop 2 return_GongJianSuShe: [DISABLE] aob_GongJianSuShe: db 83 78 1C FF 0F 95 C0 unregistersymbol(*) dealloc(*) </AssemblerScript> </CheatEntry> </CheatEntries> </CheatEntry> <CheatEntry> <ID>255</ID> <Description>"奥日无限跳--可自定义跳跃次数(初始4连跳)"</Description> <Options moManualExpandCollapse="1"/> <VariableType>Auto Assembler Script</VariableType> <AssemblerScript>// Game Exe文件名 : oriandthewillofthewisps-pc.exe // Author : laoz // Exe 文件版本 : 2018.4.11.45208 // Module Version : // Script Date : 2022-05-20 // Created with : customAOBInjectionTemplates version: 1.3.9 [ENABLE] ////=========================写入跳跃次数的第二条指令========================= //注入点位置是写入跳跃次数的第二条指令。该指令判断落地后,写入奥日的可跳跃次数。 aobscanmodule(aob_TiaoYueDiErZhiLing,GameAssembly.dll,FF FF 89 83 94 00 00 00) registersymbol(aob_TiaoYueDiErZhiLing) //意思是:跳跃第二条指令 alloc(newmem_TiaoYueDiErZhiLing,256,GameAssembly.dll) label(return_TiaoYueDiErZhiLing) //以下人造指针1 alloc(TiaoYueDiErZhiLing_P,8) //人造指针8或4字节(64位需要8字节) registersymbol(TiaoYueDiErZhiLing_P) // //以上人造指针1 //以下存放玩家指定的跳跃次数 alloc(TiaoYueDiErZhiLing_JumpCiShu,4) //跳跃次数 registersymbol(TiaoYueDiErZhiLing_JumpCiShu) //跳跃次数 //以上 label(TiaoYueDiErZhiLing_YDM) //原代码 newmem_TiaoYueDiErZhiLing: //以下进行人造指针------------------------------------------------ mov [TiaoYueDiErZhiLing_P],rbx //以上进行人造指针------------------------------------------------ //------------------------------------------------------------------- //这里4连跳,比游戏多1跳! cmp [TiaoYueDiErZhiLing_JumpCiShu],0 //比较存放我的跳跃次数的地址是否内容为0 jnz TiaoYueDiErZhiLing_YDM //不为0,则跳到原代码执行 mov [TiaoYueDiErZhiLing_JumpCiShu],3 //为0,则将4连跳写入地址.用户可以在CT表中手动改 //------------------------------------------------------------------- TiaoYueDiErZhiLing_YDM: mov eax,[TiaoYueDiErZhiLing_JumpCiShu] //------------------------------------------------------------------- //以下为原代码 mov [rbx+00000094],eax jmp return_TiaoYueDiErZhiLing aob_TiaoYueDiErZhiLing+02: jmp newmem_TiaoYueDiErZhiLing nop return_TiaoYueDiErZhiLing: [DISABLE] aob_TiaoYueDiErZhiLing+02: db 89 83 94 00 00 00 unregistersymbol(*) dealloc(*) {// ORIGINAL CODE - INJECTION POINT: GameAssembly.dll+96A980 GameAssembly.dll+96A97B: E8 90 E5 FF FF - call GameAssembly.dll+968F10 // ---------- INJECTING HERE ---------- GameAssembly.dll+96A980: 89 83 94 00 00 00 - mov [rbx+00000094],eax // ---------- DONE INJECTING ---------- GameAssembly.dll+96A986: 48 83 C4 40 - add rsp,40 GameAssembly.dll+96A98A: 5B - pop rbx GameAssembly.dll+96A98B: C3 - ret } </AssemblerScript> <CheatEntries> <CheatEntry> <ID>252</ID> <Description>"跳跃次数-初始4,可手工改"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>TiaoYueDiErZhiLing_JumpCiShu</Address> </CheatEntry> <CheatEntry> <ID>253</ID> <Description>"原始连跳次数"</Description> <ShowAsSigned>0</ShowAsSigned> <VariableType>4 Bytes</VariableType> <Address>TiaoYueDiErZhiLing_P</Address> <Offsets> <Offset>94</Offset> </Offsets> <CheatEntries> <CheatEntry> <ID>256</ID> <Description>"连跳次数指针扫描结果"</Description> <Options moAlwaysHideChildren="1" moManualExpandCollapse="1"/> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043613B8</Address> <Offsets> <Offset>94</Offset> <Offset>18</Offset> <Offset>10</Offset> <Offset>20</Offset> <Offset>10</Offset> <Offset>B8</Offset> </Offsets> <CheatEntries> <CheatEntry> <ID>257</ID> <Description>"指针扫描结果"</Description> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043B40C8</Address> <Offsets> <Offset>94</Offset> <Offset>18</Offset> <Offset>10</Offset> <Offset>20</Offset> <Offset>50</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>258</ID> <Description>"指针扫描结果"</Description> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043613B8</Address> <Offsets> <Offset>94</Offset> <Offset>18</Offset> <Offset>10</Offset> <Offset>20</Offset> <Offset>8</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>259</ID> <Description>"指针扫描结果"</Description> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043B40C8</Address> <Offsets> <Offset>94</Offset> <Offset>18</Offset> <Offset>10</Offset> <Offset>20</Offset> <Offset>48</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>260</ID> <Description>"指针扫描结果"</Description> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+0435C8E0</Address> <Offsets> <Offset>94</Offset> <Offset>18</Offset> <Offset>10</Offset> <Offset>20</Offset> <Offset>50</Offset> <Offset>B8</Offset> <Offset>18</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>261</ID> <Description>"指针扫描结果"</Description> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043613B8</Address> <Offsets> <Offset>94</Offset> <Offset>18</Offset> <Offset>10</Offset> <Offset>20</Offset> <Offset>10</Offset> <Offset>B8</Offset> <Offset>40</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>263</ID> <Description>"指针扫描结果"</Description> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+0437B130</Address> <Offsets> <Offset>94</Offset> <Offset>20</Offset> <Offset>108</Offset> <Offset>168</Offset> <Offset>38</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>264</ID> <Description>"指针扫描结果"</Description> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+04382168</Address> <Offsets> <Offset>94</Offset> <Offset>18</Offset> <Offset>10</Offset> <Offset>20</Offset> <Offset>50</Offset> <Offset>B8</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>265</ID> <Description>"指针扫描结果"</Description> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+04386530</Address> <Offsets> <Offset>94</Offset> <Offset>18</Offset> <Offset>10</Offset> <Offset>20</Offset> <Offset>E8</Offset> <Offset>0</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>266</ID> <Description>"指针扫描结果"</Description> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043876F0</Address> <Offsets> <Offset>94</Offset> <Offset>18</Offset> <Offset>10</Offset> <Offset>20</Offset> <Offset>48</Offset> <Offset>B8</Offset> <Offset>18</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>267</ID> <Description>"指针扫描结果"</Description> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+04387D00</Address> <Offsets> <Offset>94</Offset> <Offset>18</Offset> <Offset>10</Offset> <Offset>20</Offset> <Offset>50</Offset> <Offset>B8</Offset> <Offset>68</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>268</ID> <Description>"指针扫描结果"</Description> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043A2930</Address> <Offsets> <Offset>94</Offset> <Offset>18</Offset> <Offset>10</Offset> <Offset>20</Offset> <Offset>50</Offset> <Offset>B8</Offset> <Offset>68</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>269</ID> <Description>"指针扫描结果"</Description> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043A2930</Address> <Offsets> <Offset>94</Offset> <Offset>18</Offset> <Offset>10</Offset> <Offset>20</Offset> <Offset>50</Offset> <Offset>B8</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>270</ID> <Description>"指针扫描结果"</Description> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043B40C8</Address> <Offsets> <Offset>94</Offset> <Offset>18</Offset> <Offset>10</Offset> <Offset>20</Offset> <Offset>50</Offset> <Offset>B8</Offset> <Offset>78</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>271</ID> <Description>"指针扫描结果"</Description> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043B40C8</Address> <Offsets> <Offset>94</Offset> <Offset>20</Offset> <Offset>108</Offset> <Offset>68</Offset> <Offset>118</Offset> <Offset>48</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>272</ID> <Description>"指针扫描结果"</Description> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043C8460</Address> <Offsets> <Offset>94</Offset> <Offset>18</Offset> <Offset>10</Offset> <Offset>20</Offset> <Offset>50</Offset> <Offset>B8</Offset> <Offset>68</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>273</ID> <Description>"指针扫描结果"</Description> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043C8460</Address> <Offsets> <Offset>94</Offset> <Offset>18</Offset> <Offset>10</Offset> <Offset>20</Offset> <Offset>48</Offset> <Offset>B8</Offset> <Offset>18</Offset> </Offsets> </CheatEntry> <CheatEntry> <ID>274</ID> <Description>"指针扫描结果"</Description> <VariableType>4 Bytes</VariableType> <Address>"GameAssembly.dll"+043C8460</Address> <Offsets> <Offset>94</Offset> <Offset>18</Offset> <Offset>10</Offset> <Offset>20</Offset> <Offset>48</Offset> <Offset>B8</Offset> <Offset>B8</Offset> </Offsets> </CheatEntry> </CheatEntries> </CheatEntry> </CheatEntries> </CheatEntry> </CheatEntries> </CheatEntry> </CheatEntries> </CheatEntry> </CheatEntries> <UserdefinedSymbols/> <DisassemblerComments> <DisassemblerComment> <Address>"GameAssembly.dll"+96902F</Address> <Comment>2到eax </Comment> </DisassemblerComment> <DisassemblerComment> <Address>"GameAssembly.dll"+96A5DE</Address> <Comment>rax赋值2 </Comment> </DisassemblerComment> <DisassemblerComment> <Address>"GameAssembly.dll"+9706A0</Address> <Comment>哈哈哈 </Comment> </DisassemblerComment> </DisassemblerComments> </CheatTable> }}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}}} (责任编辑:蚂蚁团队) |